Microsoft’s September 2024 Patch: The African Perspective
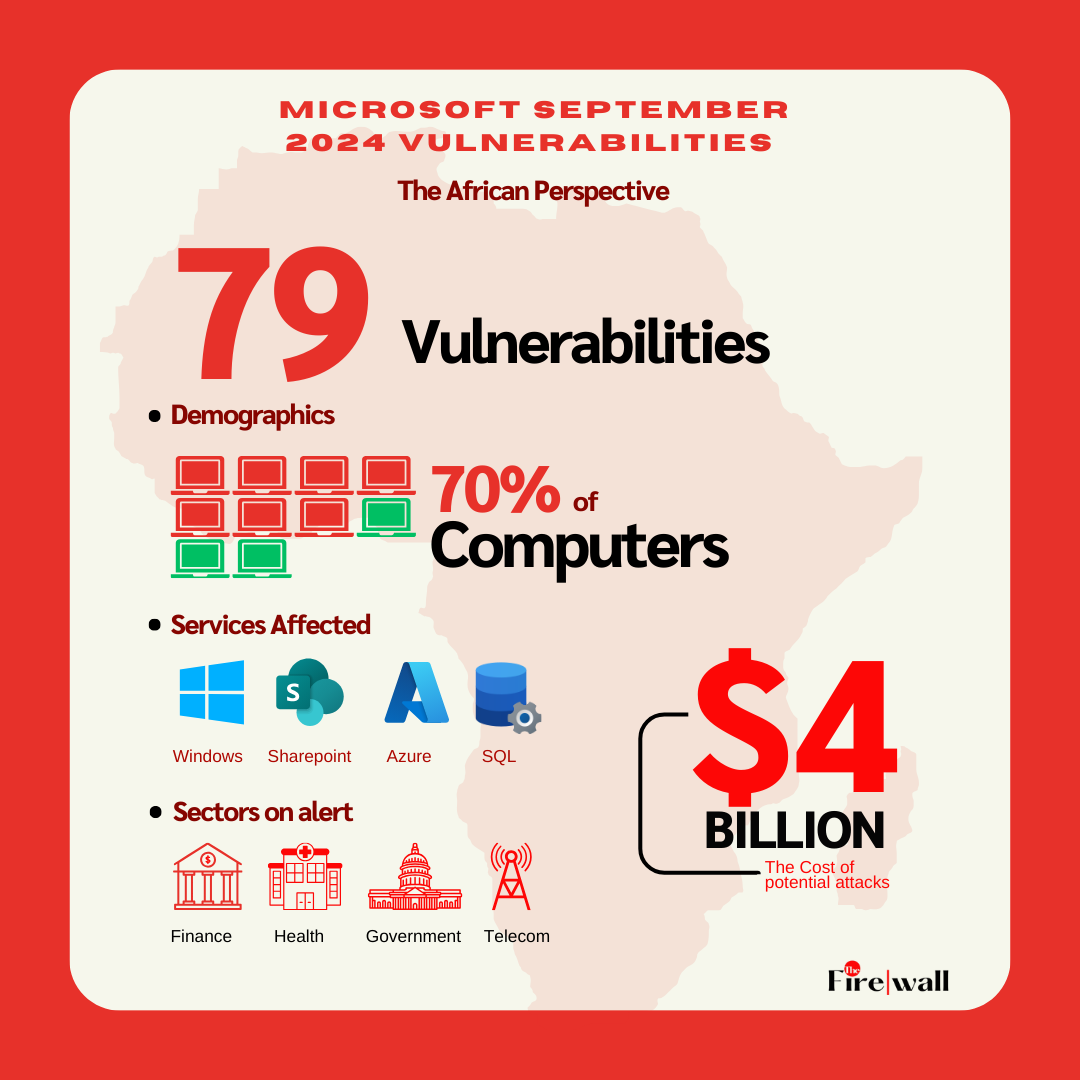
This month, Microsoft released its September 2024 Patch Tuesday updates, addressing 79 vulnerabilities, including four actively exploited zero-day flaws. These vulnerabilities affect various services such as Azure, SharePoint, and Windows Server, with some critical elevation of privilege and remote code execution flaws posing serious risks to both personal users and enterprise-level systems.
Key updates include:
Azure Stack Hub: A critical elevation of privilege vulnerability (CVE-2024-38220) that could allow attackers to gain control of Azure environments.
SharePoint Server: Remote code execution vulnerabilities (CVE-2024-38018) impacting collaboration services across organizations.
Windows Server: Critical updates that could enable remote code execution, particularly targeting Windows Server installations like Server Core.
Why Does This Matter for Africa?
Microsoft products, from its ubiquitous Windows operating system to Azure cloud services, have established a strong presence across Africa. As the primary OS on 60-70% of computers in major African countries like Nigeria, South Africa, and Kenya, millions of businesses and government institutions rely heavily on Microsoft’s software for daily operations. In the financial, healthcare, and telecommunications sectors, Microsoft products are integrated into critical workflows, underscoring the continent's reliance on these technologies. The growing adoption of Azure Cloud Services, particularly with data centers in South Africa, further cements Microsoft’s foothold across the region.
Given this dependence, vulnerabilities addressed in Microsoft's Patch Tuesday—like those in the September 2024 release—pose significant risks to day-to-day operations. Failing to apply these patches leaves African businesses and governments vulnerable to cyberattacks that could disrupt services, compromise data, and cause severe financial losses. With $4 billion lost annually to cybercrime in Africa, timely attention to Microsoft’s Patch Tuesday is essential for the protection of critical systems and infrastructures.
The sheer scale of Microsoft’s presence across Africa highlights the importance of regularly applying updates and patches, as businesses and governments cannot afford the consequences of neglecting cybersecurity, especially given the continent's rapidly evolving digital sector. Moreover, with ransomware attacks becoming more frequent globally, African organizations are at a growing risk. The reliance on older server systems in some firms also leaves them vulnerable to these newly discovered threats.
The Way Forward: Responding to Microsoft’s September Patch Tuesday Vulnerabilities
With the critical vulnerabilities exposed by Microsoft's September 2024 Patch Tuesday, organizations need to act swiftly to protect their systems. This particular update, addressing 79 vulnerabilities, including 4 actively exploited zero-days, is a wake-up call for businesses and government institutions that rely heavily on Microsoft products. What’s next?
Immediate Patch Implementation: Organizations should prioritize applying the September patches to all affected systems. IT teams should focus on the critical vulnerabilities, especially those related to remote code execution and elevation of privilege, which could allow attackers to gain control over systems. Delaying these updates risks leaving critical infrastructures—such as finance, healthcare, and telecommunications—exposed to cyberattacks.
Vulnerability Prioritization:
Given the complexity and number of vulnerabilities, it's crucial for organizations to prioritize systems based on their risk profiles. For example, patches affecting Windows Servers and SQL Servers should be immediately applied, as these often house sensitive data and run mission-critical operations.Strengthening Patch Management Processes:
Organizations need to move from reactive to proactive patch management. This involves automating updates where possible and ensuring there's a defined schedule for testing and applying patches. Automated patching tools can help reduce the operational burden, while still ensuring vulnerabilities are addressed in a timely manner.Enhance Cybersecurity Monitoring: As vulnerabilities can sometimes be exploited before patches are applied, businesses should invest in real-time monitoring and threat intelligence tools that can detect abnormal activity, such as those linked to zero-day exploits. This will enable quicker detection and response to potential breaches.
Backup and Disaster Recovery Plans: Since some attacks target business continuity by corrupting or locking critical data, it’s vital to have robust backup systems in place. Regular data backups, stored offline, will help organizations recover quickly in case of an attack, minimizing the impact of data loss or system downtime.
Promote Cybersecurity Awareness: Patch Tuesday vulnerabilities emphasize the importance of cybersecurity awareness. Employees should be regularly trained on best practices, such as recognizing phishing emails, which often serve as entry points for attacks exploiting vulnerabilities. This is particularly important in Africa, where digital literacy may vary significantly across sectors.
As digital adoption continues to rise, these steps are essential to safeguarding Africa's future in an increasingly interconnected world. Ultimately, vigilance and proactive response to vulnerabilities will ensure that the continent remains resilient against the evolving landscape of cyber threats.